GIJN is offering a unique cyber reporting training program specifically tailored for investigative reporters. The course is free and limited to 20 participants. It will take place each Monday and Thursday for six consecutive weeks at 10 am EDT, starting on May 08, 2023. Apply here.
Tools & Techniques
Online Research Tools and Investigative Techniques
|
Search engines are an intrinsic part of the array of commonly used “open source” research tools. Together with social media, domain name look-ups and more traditional solutions such as newspapers, effective web searching will help you find vital information. Many people find that search engines often bring up disappointing results from dubious sources. A few tricks, however, can ensure that you corner the pages you are looking for, from sites you can trust. The same goes for searching social networks and other sources to locate people.
مقالات عربية
دليل المحقق اليومي
|
أخبار الإعلام:
تويتر يعلق نحو 500 حساب بتهمة “التلاعب المنظم”
قام تويتر بتعليق 486 حسابًا جديداً حيث يواصل حملته ضد الأخبار المزيفة و “التدخل الأجنبي”. يأتي هذا عقب تعليق 284 في 21 أغسطس.
Data Journalism
The Research Desk: Tips and Tools
|
The Research Desk with Gary Price is back, with its second installment, featuring a roundup of new tools — the WHO’s MiNDBANK database, with documents from 170 countries; ePSIplatform, on open data in the EU & worldwide; new UN report on wastewater; NATO archives expand; and the Getty Thesaurus of Geographic Names.
Data Journalism
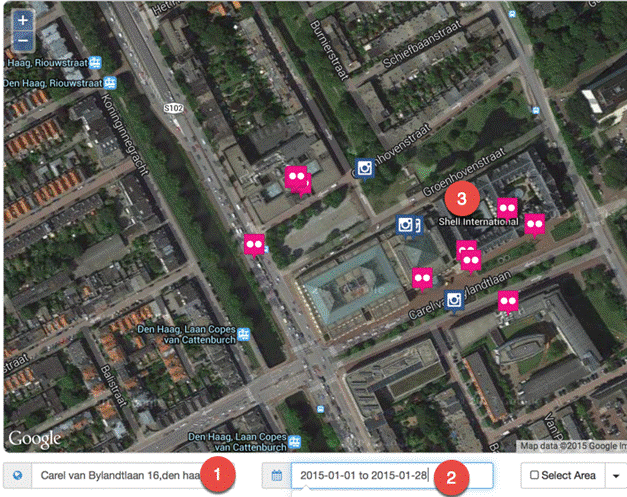
Online Methods to Investigate the Who, Where, and When of a Person
|
Online research is often a challenge for traditional investigative reporters, journalism lecturers and students. Information from the web can be fake, biased, incomplete or all of the above. Offline, too, there is no happy hunting ground with unbiased people or completely honest governments. In the end, it all boils down to asking the right questions, digital or not. This chapter gives you some strategic advice and tools for digitizing three of the biggest questions in journalism: who, where and when?
Data Journalism
What Is Data Journalism — Journalists Offer An “Explication”
|
The good people at the Journalism in the Americas Blog, who just hosted the always interesting International Symposium on Online Journalism, alerted us to a useful new video, “Data Journalism: An Explication.” Here are journalists doing their best to define data journalism.The video comes from Cindy Royal, an associate professor, and Dale Blasingame, a lecturer, in the School of Journalism and Mass Communication at Texas State University.
dark web
Document of the Day: U.S. Secret Service Contract for “Dark Web” Research
|
Paper trails have always been of great interest to investigative journalists. Digging into documents can tell a great deal about people, organizations, and what they’re up to. Here’s today’s Doc of the Day, a contract recently filled by the U.S. Secret Service, the law enforcement group charged with protecting the president and other political VIPs. It’s for “Dark Web Data Subscription.” More than 90% of the Web is thought to be unsearchable by Google and other common search engines. This is often called the dark or deep Web, and it includes sites behind firewalls and passwords, unusual formats, criminal and other hidden networks, and lots and lots of databases.
tips & tools
GIJN Launches Help Desk
|
From GIJN’s earliest days, its global community has been rooted in a collaborative and generous spirit, with journalists around the world sharing ideas, sources, and stories. To help deal with the growing demand for assistance, GIJN has created a formal Help Desk to better marshal its resources and tap the expertise of its global network. The staff reached out to hundreds of trainers and experts who have spoken at GIJN conferences to create an international database of experts on investigative and data journalism.
Security
Wi-Fi Can Be Dangerous: Three Ways To Avoid Getting Hacked
|
Fast Company last week brought home the issue of online privacy with a chilling piece on in-flight eavesdropping. It turns out that USA Today’s Steven Petrow, while working on a story on the Apple-FBI battle over iPhone access, “had been hacked mid-flight” over an American Airlines Wi-Fi system.
Security
Data at Risk: How To Protect Your Sources and Your Work
|
Information stored on your computer or mobile is at risk. You could leave it on a train; it could be seized at an airport security checkpoint; or by the police or courts. And of course hackers can access your data. You need to be aware of all the risks and ways to protect your information, your sources and yourself.
Methodology
Environmental Investigative Reporting: Resources & Methods
|
In this just-released video, investigative reporter Mark Schapiro goes in-depth on how to use investigative techniques in probing often complex environmental issues. Schapiro, a veteran of the original Center for Investigative Reporting, gave this talk in Hamburg at NR15, the July 2015 annual conference of Netzwerk Recherche, Germany’s investigative journalism association.