
Guard your walls. (Peter Levy)
Protecting Yourself Without Losing Your Mind
The author’s list of tools is here.
Digital self-defense is becoming an important part of the journalistic toolkit. Beyond risks to everyone’s digital lives—webcam hacking, email breaches, identity theft—people who work in newsrooms have even more at stake. Newsrooms are some of the biggest targets in the world for state-sponsored digital attacks, as well as more routine threats.
But security is not about locking everything down. It can feel overwhelming if everything is under threat. Instead it’s about making it harder to access information that is especially important to secure. There is no such thing as “perfect security.” Instead, it’s more about building stronger roadblocks, and making it harder for others to access our data without consent.
For further information, including links to many helpful sources, see the GIJN Digital Security resource page.
Focus on Specific Threats
Consider the information you want to protect, who might want it, what ways that information can be compromised, and what you can do to address the security gap. Security specialists call this practice threat modeling.
Rather than thinking about security in the abstract, thinking about a threat model can help journalists to focus on specific problems and solutions. For example, with few exceptions, most of us are not likely to be directly targeted by three-letter agencies. Instead, most of us might be more cautious about our sources being identified in connection with specific stories. Many of us need to open countless documents through email each day, yet need to avoid malicious files or links. Many of us simply want to avoid an embarrassing public-facing data breach.
Understand Encryption
Using encryption is one of the most effective ways to make it harder for others to access our data.
Encryption helps protect the content of your messages shared between you and other services online. Imagine if you sent a postcard, leaving the text readable to anyone who wants to read during its journey. The internet works in a similar way. For example, when connecting to an open wi-fi access point, anyone on the network can see the flow of unsecured traffic in readable text.
So what do we do? Most of the time, we’re doing routine work and may not be on high alert. Even in those cases, we still want to minimize our data footprint from surveillance.
Connect to the Web More Safely

- Especially when you’re on an open wi-fi network, consider using a Virtual Private Network (VPN) for an encrypted connection that will tunnel all your traffic through a remote location. That remote location can still read your unencrypted traffic, but it will be encrypted on your local network. This can be helpful for protecting your traffic when visiting conferences or cafes. There are no shortage of inexpensive services that can help protect your Web traffic from local network snooping. You might also check if your newsroom uses a VPN so you can tunnel through their network.
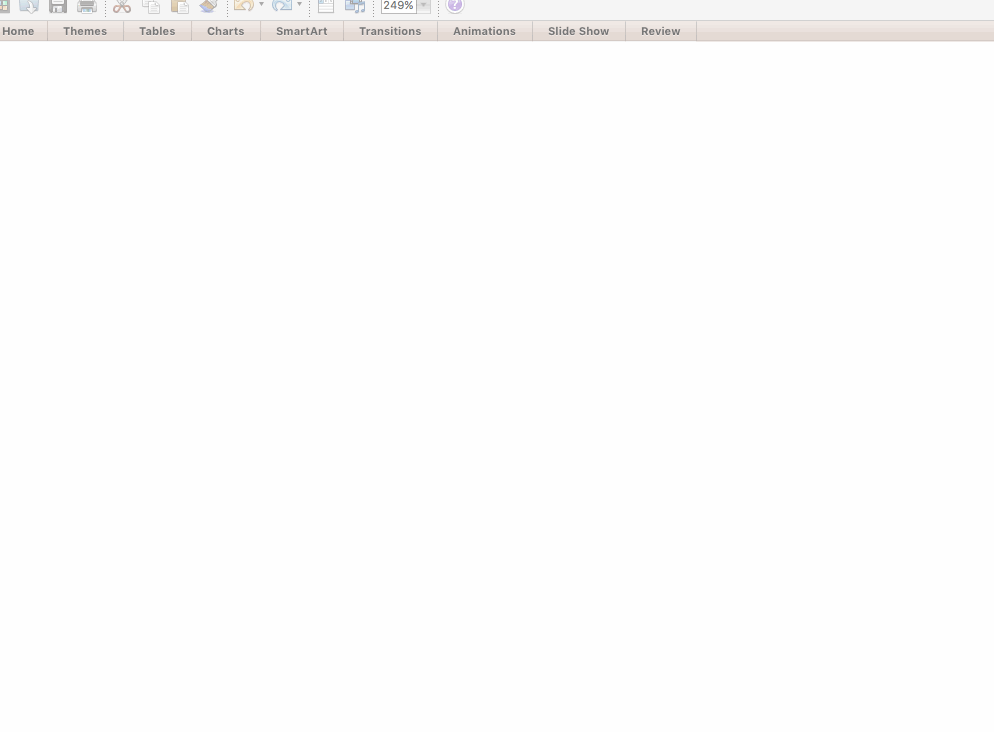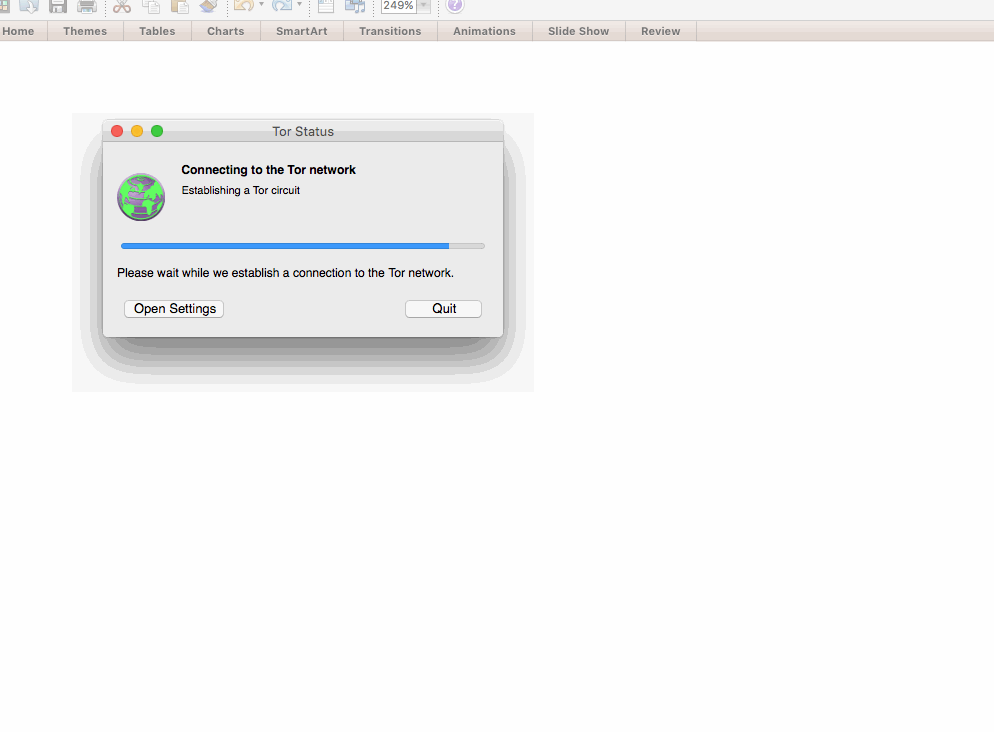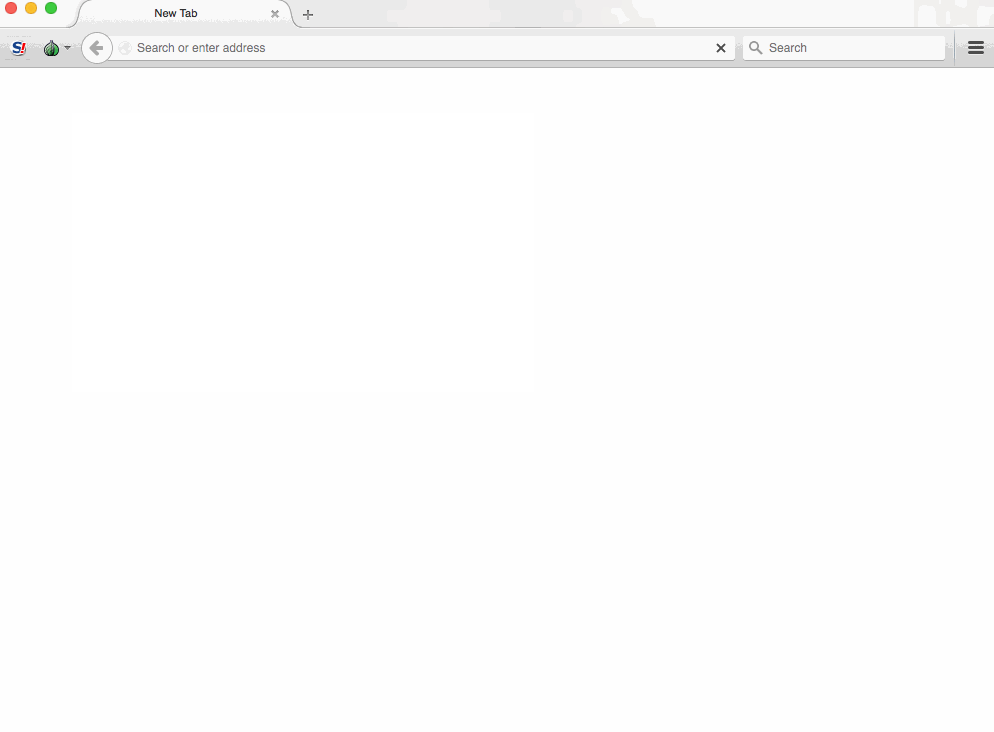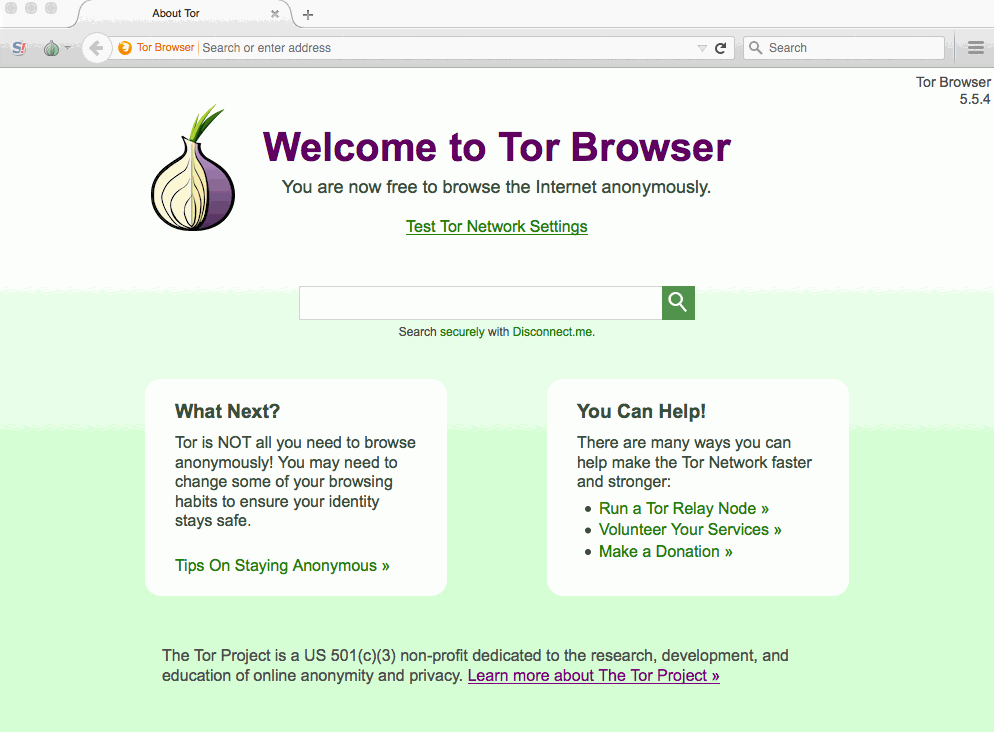
- If you’re conducting research, you can often be identified through unsecured traffic, as well as other loose identifiers such as your IP address. Consider using Tor Browser to encrypt and anonymize your Web traffic. With Tor, your browsing traffic will appear to come from a remote location, and will be encrypted on your local network. This can be helpful when doing sensitive research. Unless absolutely necessary, avoid putting personally identifying information into Tor Browser.
Use Strong Authentication
A good password is often the only thing stopping an attacker from having access to your account.
- Everyone knows you use the same password everywhere. Stop using the same password everywhere.
- Consider using a password manager. Password managers can help you to keep track of all of your passwords, and can help generate randomized passwords. It’s also a convenient way to automatically enter passwords in your Web browser, saving time and headaches when filling out forms. Some of the most popular tools include 1Password and KeePassX (free).
- Use two-factor authentication. Two-factor authentication adds an additional level of security on top of your password, asking for one more piece of information before you can access the account. Typically this is a number sent to your phone via SMS or a mobile app, such as Google Authenticator. Countless popular Web services allow you to add two-factor authentication to your account, making it much more difficult for an unauthorized third party to access your account.
Use two-factor authentication wherever possible, but especially your primary email. If someone gets into your email, at a minimum, they can gain entry to your other online accounts by resetting your passwords that rely on email authentication. Gmail users can set up two-factor authentication here.
Beware of Third Parties
Of course, even a secured connection to the Web can betray our communications if the destination has the power to share consumers’ activities with a third party. For example, unless your newsroom hosts their own email servers, chances are that your newsroom uses a proprietary email provider that can decrypt your communications. Many news organizations do. Likewise, when we communicate with sources, we’re often leaving breadcrumbs about those conversations in the form of metadata – information about who is talking to whom, when, and for how long. These are not hypothetical problems for news organizations. For example, in 2013 the Department of Justice subpoenaed telephone companies for two months of phone records of reporters at the Associated Press. In other words, we often entrust our data to companies that may (willingly or unwillingly) share it with third parties.
Be Safer When Communicating
Securing your communications with colleagues and sources is becoming easier.
- If you’re concerned about the privacy of your SMS messages or phone calls, use Signal for iOS or Android to encrypt your messages. Consider asking sources to use it to speak with you; Signal is as easy to use as most default messaging applications.
- The incredibly popular WhatsApp for iOS and Android now uses end-to-end encryption. WhatsApp is using similar encryption to Signal. With hundreds of millions of users, it’s possible your sources already use WhatsApp, and you just need to add one another in the app. Bear in mind, however, that Signal and WhatsApp do not give users anonymity. (Caution: Concerns about WhatsApp vulnerabilities in 2019 prompted this advice from the Committee to Protect Journalists.)
- There are options available for encrypting your email. By far the most popular is PGP, which helps encrypt the contents of an email. When using PGP, the subject line and email address fields are not secured. The open source implementation of PGP is called GnuPG , which can be used onMac OS X, Windows, and Linux. It is somewhat controversial in the security community because it’s fairly complicated, and can take a great deal of time and effort to set up. It can also be quite easy to make mistakes that could compromise users’ security. At the moment, PGP encrypts the content, rather than the metadata in a message. Importantly, it does not protect the identities of participants in the email. In other words, PGP does not help to protect the anonymity of your sources.
Maintaining anonymity requires us to focus on metadata about our conversations.
- If you’re looking for more privacy when chatting, consider Ricochet to communicate anonymously over the Tor network. Alternatively, Tor Messenger can offer similar functionality. Tor Messenger also offers options for tunneling encrypted messages through proprietary services such as Google’s Hangouts messenger, but that’s entirely optional. These are some of the easiest tools to use for protecting metadata and the content of a message. Unfortunately if your sources reach out to you with a regular phone call, text message, or email, there is already a metadata trail. Make your contact information prominent (e.g., on articles and professional pages) so sources know you’re available through anonymous channels as needed.
- There are excellent tools for helping sources to connect or share files with journalists anonymously, such as SecureDrop, maintained by the Freedom of the Press Foundation. Of course, using SecureDrop properly requires extraordinary care on the part of the source. As The Intercept described in their primer on leaking with SecureDrop, there are many ways to accidentally leak personal data.
- Depending on your situation, speaking from someone else’s phone or simply meeting in person may be an easy way to minimize your digital footprint. These may be a reasonable solutions if you’re concerned about “smaller” security threats.
Routine Privacy and Security
A lot of the easiest ways to protect yourself online require one-time setup. Afterwards, the security benefits require relatively little effort.
- Many unsecured HTTP websites also have secured HTTPS versions of the site available. Download HTTPS Everywhere for Firefox or Chrome to quietly upgrade these connections when browsing.

- Many websites will passively track your whereabouts using files called cookies, which are saved to your browser as you traverse the Web. Altogether, these cookies can give a pretty accurate composite of the places where you go online. You can easily block tracking cookies using Privacy Badger for Google Chrome or Firefox.
 If you’re concerned about your files on third-party servers, consider using “zero-knowledge” cloud
If you’re concerned about your files on third-party servers, consider using “zero-knowledge” cloud
services that can host your data, while preserving privacy because they do not have the keys to decrypt your data. For example, SpiderOak passively backs up files, much like Dropbox. Likewise, the zero-knowledge serviceCrashPlan can back up your hard drive in case you lose access to the device. There is a tradeoff: with most zero-knowledge services, you cannot easily recover your account if you forget your password. It’s important to keep your password somewhere accessible and secure.- Take a close look at the URLs in links before you click them. If something looks odd, go with your gut; you might have gotten a fake link disguised as your desired destination. Hackers depend on our slip-ups to send us to fake phishing websites where we might enter our legitimate username and passwords. For example paypal.com paypal.server1314.com and paypa1.com (with a 1) can look quite similar without being vigilant. The Freedom of the Press Foundation published an excellent guide with more details about how to defend against phishing.
- When you’re suspicious of a document you’ve received (e.g., over email), tempting as it may be, don’t launch it on your computer. Again, be on the lookout for malware before executing files. Ask yourself whether the file extension makes sense. If the person is sending a .exe file for a document that you would expect to be a .pdf or .doc, something might be wrong. Even legitimate-looking files can launch malware. Rather than executing suspicious documents on your computer, consider using Google Docs to open them. If you’re okay with Google having access to the file, this can be a quick and effective way to look at documents safely.
- Of course, keep your devices, software, and antivirus updated regularly. Consider making critical updates automatic whenever possible. It’s one of the most important things journalists can to do stay a step ahead of attackers. Hackers, researchers, and security companies are constantly identifying new holes in software, and those holes can sometimes be exploited by malicious actors to access vulnerable systems. Updates may be annoying, but can be an easy way to patch these holes.
Encrypt Your Devices
If someone steals your unsecured device, it’s easy to access your files or copy your hard drive. Luckily, it’s also easy for journalists to encrypt their devices. If you own a newer iPhone and have a passcode, there’s a good chance your phone is already encrypted. You can also learn how to encrypt your Android device here. If you use Mac OS X, you can encrypt your drive using FileVault. Likewise, if you’re a Windows user, some versions allow you to encrypt your drive with BitLocker.
Lastly, do the things you know you should. I’ve visited multiple newsrooms where journalists did not lock their terminals when walking away from the computer. (On Windows, lock your terminal with Windows+L. On Mac, use hot corners to quickly lock your terminal.) Avoid putting unknown USBkeys into your machine, or launching files from people you don’t know. They may contain malicious software.
Start Simple, Start Now
There is no “one size fits all” solution to digital security, but this should help you get started. Learn more about how to protect yourself by investigating security resources. These simple security habits can help make your newsroom a safer environment. This is about ensuring the trust and safety of sources, and minimizing the likelihood of exposing your newsroom’s data to intruders. Fundamentally, this is about doing more effective journalism by understanding the channels through which your information flows, and how to better control it.
This story originally appeared on the website of Source and is reprinted with permission.
 Martin Shelton is a 2016 Knight-Mozilla OpenNews Fellow working with the Coral Project at the New York Times. Martin maintains the Tinfoil Project, a community for learning about journalism and information security. He has previously worked with Google‘s Privacy Research and Design team, Pew Research, and Twitter as an intern.
Martin Shelton is a 2016 Knight-Mozilla OpenNews Fellow working with the Coral Project at the New York Times. Martin maintains the Tinfoil Project, a community for learning about journalism and information security. He has previously worked with Google‘s Privacy Research and Design team, Pew Research, and Twitter as an intern.
